This post will cover the process of adding untrusted servers into your SCOM 2012 R2 environment. This guide is not for adding servers via a Gateway Server, this guide will show you how to add servers on the same network as the SCOM Management Servers but not necessarily trusted by the domain.
First, you need to have created a SCOM Client Cert. See my previous blog
And you need to have setup your Manage Server.
Overview of the Process
- Import Root CA Certificate to untrusted server.
- Generate SCOM Client Certificate for Untrusted Server(s).
- Import SCOM Client Certificate to Untrusted server Personal certificate store.
- Install SCOM Agent to untrusted server.
- Import SCOM Client Certificate with MomcertimportTool.exe.
- How to Confirm Certificate imported correctly.
- Open SCOM Console and Verify connection.
- Approve Agent.
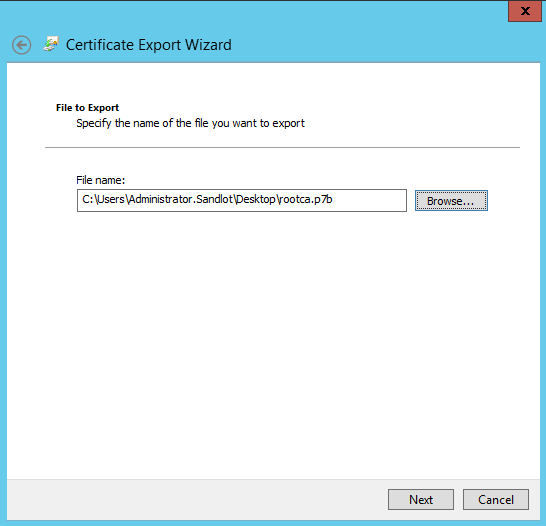
1. Export the Root Certificate
Export the Root Certificate Chain and save to a convenient location. Open MMC on a domain trusted computer and navigate to Trusted Root Certificate Authorities, find your Root CA and right click Export. You can also download the chain from your Certificate server web page, by clicking download and then download full certificate chain.
Export it and save it to a location you can reach on your untrsuted servers.
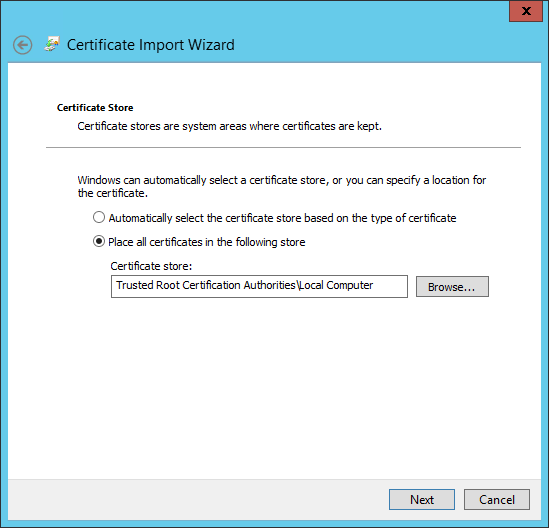
Login to your untrusted server and open MMC, expanded Trusted Root CA and right click it and click Import.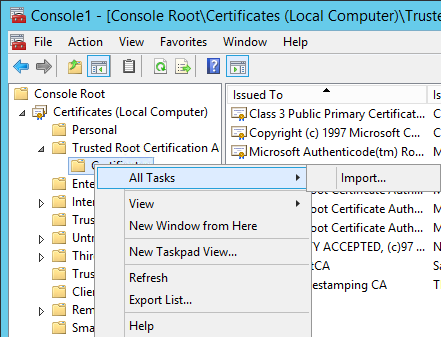
Click next on the wizard till you can import the Certificate. Find the certificate.
Once imported find the Certificate, right click the certificate and select properties. If you see a red x on the certificate, you have a problem, you should try it again and if you continue to have issues talk to your AD Expert or if you don’t have one, consult your favorite search engine.
2. Generate SCOM Client Certificate for Untrusted Server(s).
This is where many of the guides I followed fell apart for me. Many of them have you going to the certsrv webpage on the domain controller. There are several problems with this, Internet Explorer on servers by default and rightfully is completely locked down. There could be issues resolving the webpage and so on and so forth. So my recommendation is from your SCOM server, or another domain joined PC go to https://FQDN/certsrv or open MMC and load the certificates snapin.
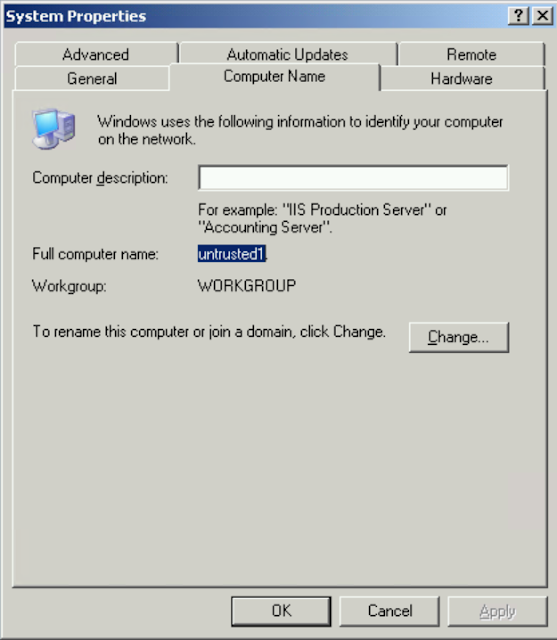
This is another place where the guides were unclear. You need to get the computer name of the untrusted computer. If the server is not in a domain you just want that name, if it is in another domain you want the FQDN. My recommendation is to go into system properties and copy exactly whats in the field for computer name.
Some of the guides keep saying get the FQDN, using FQDN implies you need the domain suffix even if the server is not in a domain. In my previous post I mentioned that you need to be able to ping the untrusted server from the SCOM server, meaning you need to add an A record in your DNS. So in my example there is an entry in my lab’s DNS of untrusted1.sandlot.dom. Do not add the FQDN unless the untrusted server you are attempting to monitor is actually in a domain.
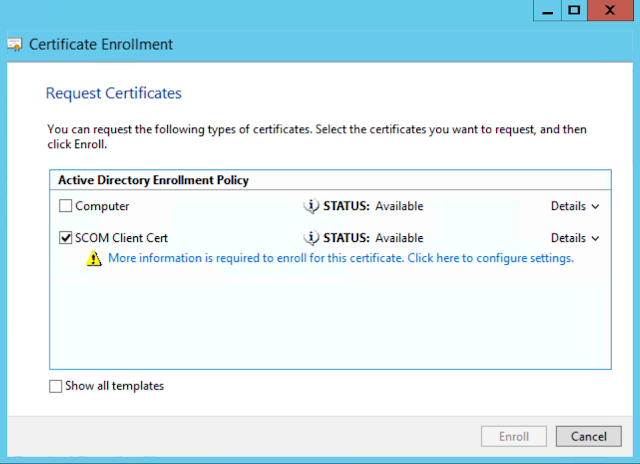
Once you have the server name open MMC or the Certsrv webpage and request the SCOM Certificate. In my example I will use MMC. Load the certificates snapin for local computer.
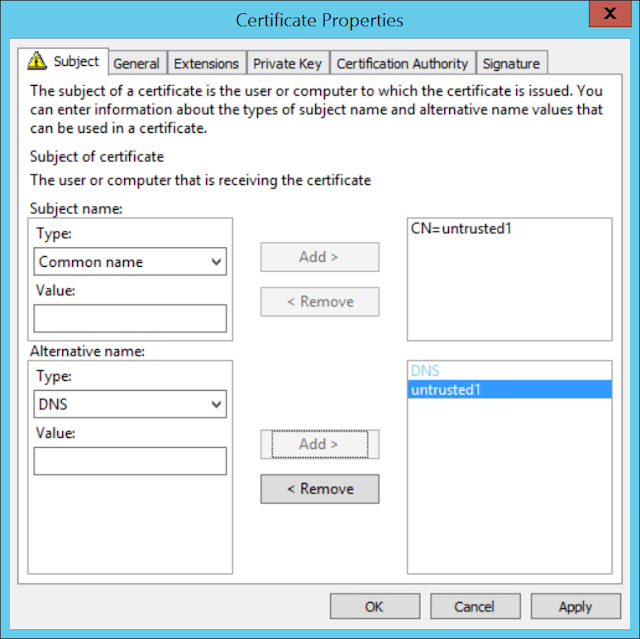
Select the SCOM Client Cert and click on the blue text to fill in the extra information the certificate needs.
On the Certificate Properties window under the Subject page, select Common Name and DNS name and add your server name, in my case “untrusted1”
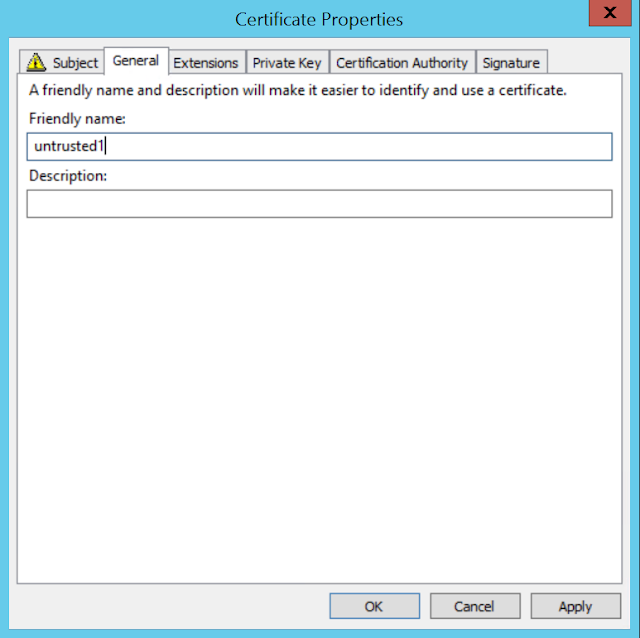
Then select the General Page and add your server name there as well.
Click ok, then finish the wizard with defaults.
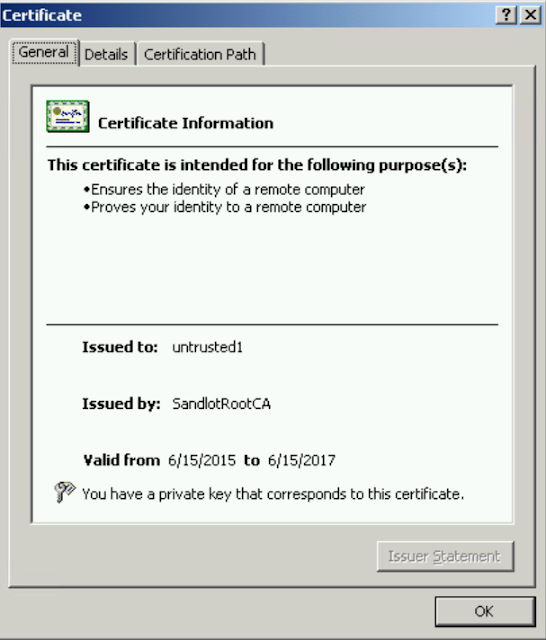
Under Personal Certificates you should now have a certificate named after your server name, in my case “untrusted1”
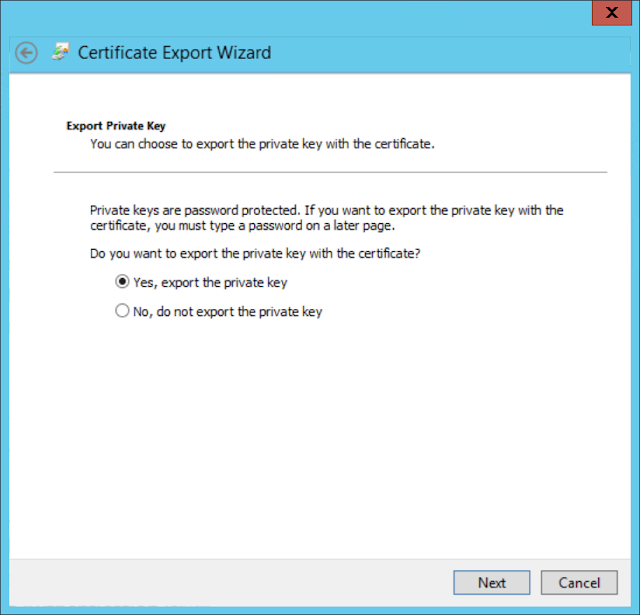
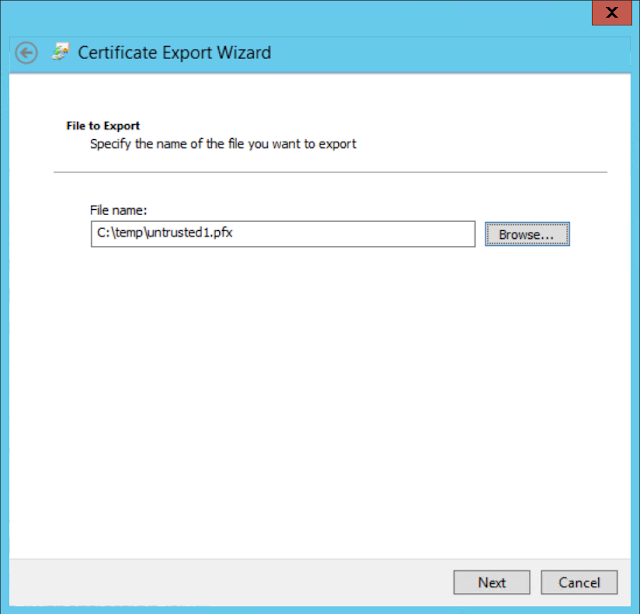
Right click your certificate and click export.
Select Yes, export the private key (this is absolutely necessary, without the private key there is no trust when using the certificates.)
Select export all extended properties, you can, but it is not necessary to export all the certificates in the chain. You should have already imported the Root CA certs prior to this step.
Save it somewhere that is accessible from the untrusted server.
3. Import SCOM Client Certificate to Untrusted server Personal certificate store.
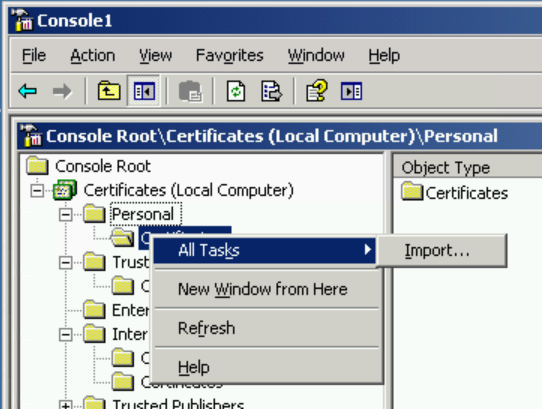
On your untrusted server copy the certificate you just created to the local server. Open MMC and load the Certificates snapin for local computer. On Personal right click and select All Tasks -> Import.
The Import Wizard will appear.
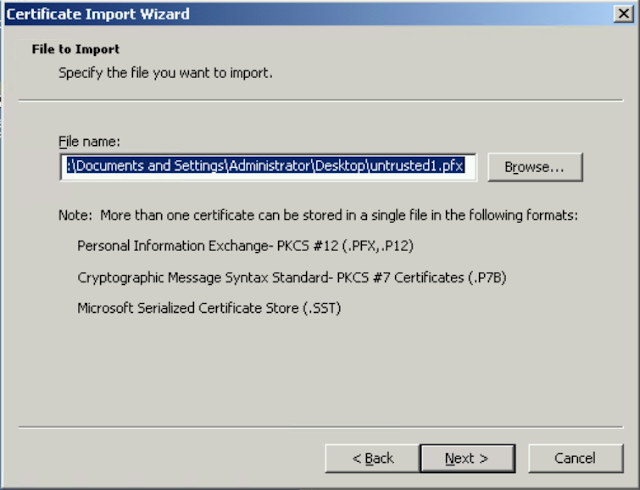
Click Browse and select your certificate.
Select Next and enter your password on the next screen.
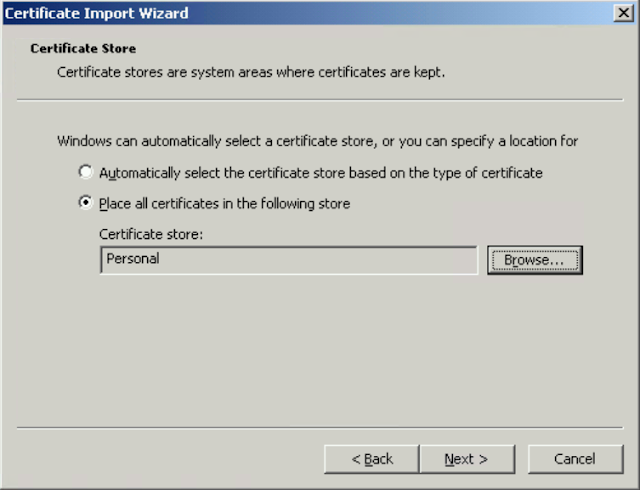
Select Place All Certificates in the following Store, click browse and select personal store.
Back in MMC open the certificate, if you seen green, you are good. If there is red, you may need to check that your Root CA certificates imported successfully or that you exported your server certificate with the Private Key.
4. Install SCOM Agent to untrusted server.
Now that the Certificate is imported, navigate to your SCOM server or SCOM installation media and find your x86 or AMD64 agent installation folder. Click on Momagent.msi If you get an error about needing the Core MSXML 6.0, the install is in the same folder, its called MSXML6.msi
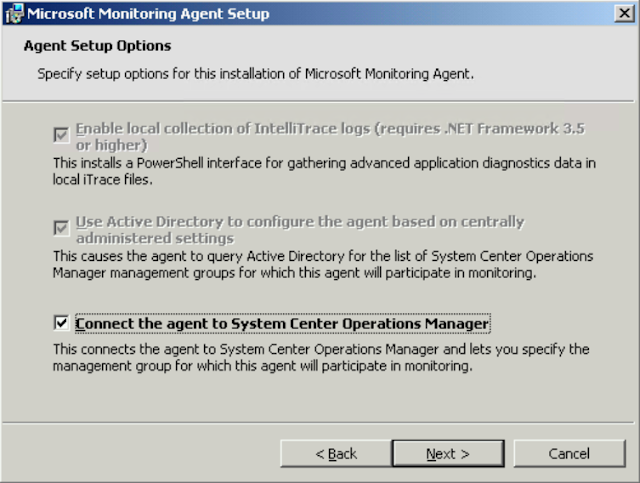
Enter your Management Group Name and your FQDN of your Management Server.
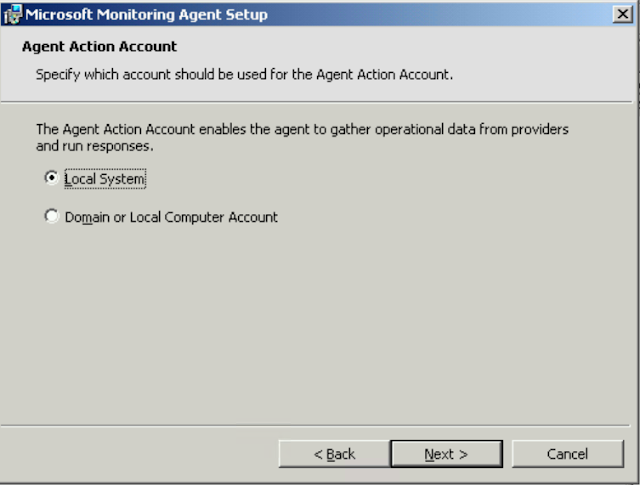
Select Local System.
5. Import SCOM Client Certificate with MomcertimportTool.exe.
Now, you need the Momcertimporttool.exe which lives under the Support Tools folder on the SCOM installation media. I usually copy this to the same level under the SCOM installation folder. Remember you need the corresponding x86 or amd64 version of the tool for your server. Copy the .exe to your untrusted server, open a command prompt and navigate to the folder where it is located. then type momcertimportool.exe /subjectname yourservername
I would recommend always typing the /subjectname instead of just typing momcertimport.exe and selecting the certificate, I have seen this method not work consistently.
You can verify successful installation of the certificate the same way as for the Management servers. Restart the Microsoft Monitoring Agent Service on the untrusted server and then check the Operations Manager section of the Event Viewer for event 20053. You can also view the registry for the reversed pairs of the certificate. Refer to my previous post on how to do this.
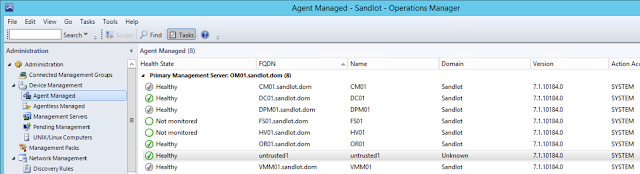
After a few minutes you will have your untrusted server under Pending Management on the Administration Page, approve it if you don’t have SCOM set to automatically approve.
After SCOM communicates with the newly installed agent and downloads the necessary management packs the agent will show as green in SCOM and start alerting on any problems on the server.
I hope you found this guide helpful. If you have any questions or need any help with this convoluted process please feel free to leave a comment or email me directly.